Today we are talking about hacking OS (Operating System). Have you just thought, how can we work on a laptop and PC without an OS? So we really can’t work on a laptop or PC without an OS? So, let’s first see what this OS is. Why do we use OS? O/S (Operating System) or operating system means someone who combines hardware and software. It is exactly right. It means something like this
You don’t know all the hardware details of your laptop PC, do you? Hardware is a very complex thing. We can’t remember them at all. Meanwhile, the software / applications that we install on laptops and PCs are made by different companies. But they can be run on our laptop PC. How did that happen?
This is what happens. We install the OS on our laptops and PCs. Then the OS works as an intermediary between Applications / Software and Hardware. Application does not know about hardware. Hardware does not know about the application. So the OS connects these two. That’s why software/applications made by different companies can be easily installed and used on our laptop PCs.
But even though the OS connected these two like this, two other people who we don’t talk to much help in this work. That is API (Application programming interface) and ISA (Instruction set architecture). The API is between the application and the OS. ISA is between the hardware and the OS.
The API can easily extract the details of the file system. ISA can easily find the hardware details. So both of them inform the OS what they detect in this way. As a result, the OS creates an interface or an abstract layer that is easy for us to work with.
Apart from that, there is another task that the OS does and that is resource management. What happens is that when we do each task on the laptop or PC, disk space, memory, network, bandwidth etc. are distributed accordingly.
So this is how the OS helps to make our work easier by providing an abstract layer and resource management to do our work.
Now let’s see about hacking OS. When talking about Hacking OS, we have to forget about Windows and Mac OS. Do you know why? Hacking tools cannot be run on Windows and Mac OS.
So let’s look at the OS of the Linux family, which many people call hacking OS. Although many people say hacking OS, but these are not actually OS made for hacking. These are made for penetration testing. So, because hacking tools can be run on the OS made for penetration testing, many people call it hacking OS. Now let’s look at Kali Linux which we all know.
Kali Linux
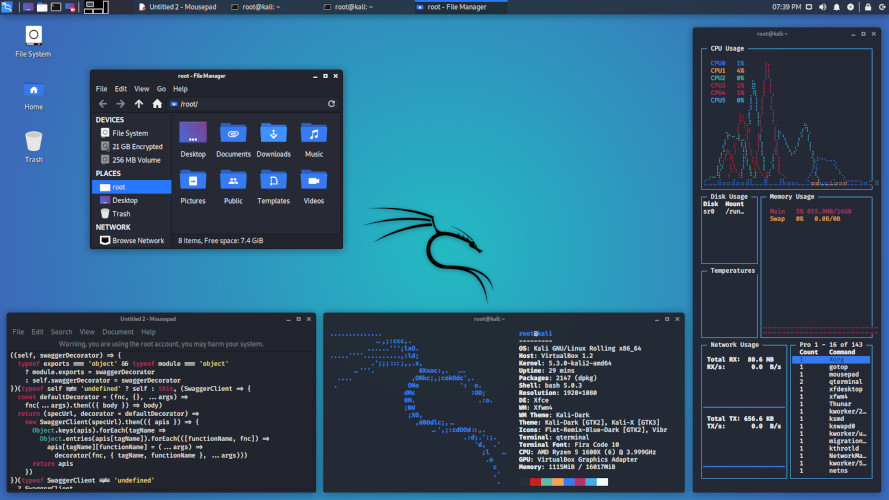
What is Kali Linux? Kali Linux is a Debian-based Linux distribution of the Linux family created in 2013 by Offensive Security.
So what is this Linux distribution?
You have heard, haven’t you, that there are different versions of Windows. That means Windows 7, Windows 8, Windows 10, Windows 11.
But such versions do not come in Linux environment. But why is that happening? Windows is a software that we have to pay for. That is not open source. That is why the new version of Windows OS is updated by Microsoft company. Others cannot interfere in the work of updating its version.
Linux is an open source OS. That means you can download it for free. That’s why many developers buy the original Linux Kernel and change it. So we call those new versions that they have made as they want Linux distribution.
Also, the Original Kali Linux environment includes XFCE, GNOME free user defined interface and can work in KDE as well. Looking at the system requirements, offensive security says that 1GB of RAM and 20 GB of hard disk space are required as minimum requirements.
Not only that, according to the Offensive Security Company, Kali Linux has more than 600 Pentesting tools. Among them, tools like password attacks, exploitation tools, web application tools, hardware hacking tools, wireless attacks, information gathering, vulnerability assessment have become famous among many people.
Parrot OS
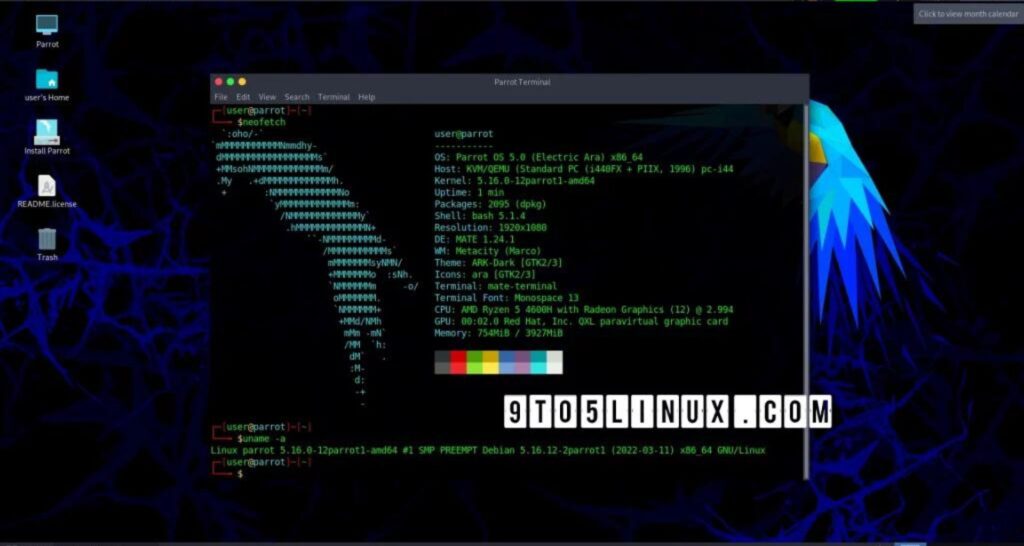
What is this Parrot OS that everyone is talking about? Parrot OS is a Debian-based Linux distribution just like Kali Linux. This is made by the Parrot OS Developer team led by Lorenzo. That was in 2013. Not only that, this is also an Open Source OS like Kali Linux. When you look at the desktop environment of Parrot OS, you will find GNOME and XECF default. We can also run this in KDE.
If you are installing Parrot OS, according to the Parrot OS developer team, 320 MB RAM and 16 GB hard disk space are required as minimum requirements. When it comes to Parrot OS, it has become famous among many people. What do you know?
An organization that issues many professional certificates on the Cyber Security side is called EC-Council. So many people in the Cybersecurity side do the CEH (Certified Ethical Hacker) certificate from the EC-Council.
So the EC-Council, which provides the opportunity to do the CEH exam in this way, has recommended to use Parrot OS in their exam. They have mentioned 5 things as reasons for that.
According to them, due to the Parrot OS, we have been able to easily create each and every program we need for the hacking side. Also, our privacy is very secure when we use the internet. Not only that, the CE-Council recommends Parrot OS because it has more tools than Kali Linux, because it has a better interface and because of its higher performance.
Back Box

Now let’s see who this back box is.
Back box is also a Debian-based Linux distribution like Kali Linux, Parrot OS. Also, the first black box distribution was released in September 2010, with the contribution of the black box team. Not only that, but according to the black box team, XFCE default is found as the desktop environment of the black box OS.
Black box is an Open Source OS as we talked about earlier. Not only that, according to the black box team, this OS has included many functions such as security and analysis tools, web application analysis tools, network analysis tools, and vulnerability assessment tools.
The Black Box team has now developed their Black Box OS to work on the Amazon web service cloud platform.
Black Arch
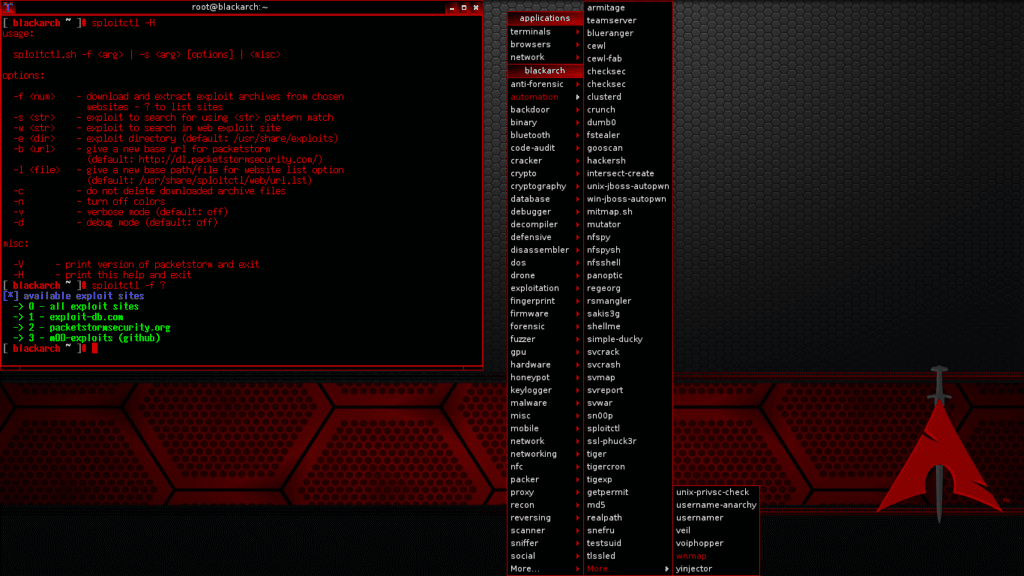
Now let’s see what this Black Arch is.
Black Arch is an Arch based Linux distribution that helps in penetration testing just like the OS we talked about earlier. This is also an Open Source OS like the OS we talked about earlier. The special thing about this is that there are about 2751 tools for those doing penetration testing.
Not only that, according to the team that made black arch, XFCE default is found as the desktop environment of black box OS. If you look at the tools available in this OS, 0d1n, 0trace, 3proxy, 3proxy – win32, 42 zip, a2sv, dorkme, dornet, firecat , firefox – many things like decrypt, find3, khc, keya have become famous these days.
Live hacking OS
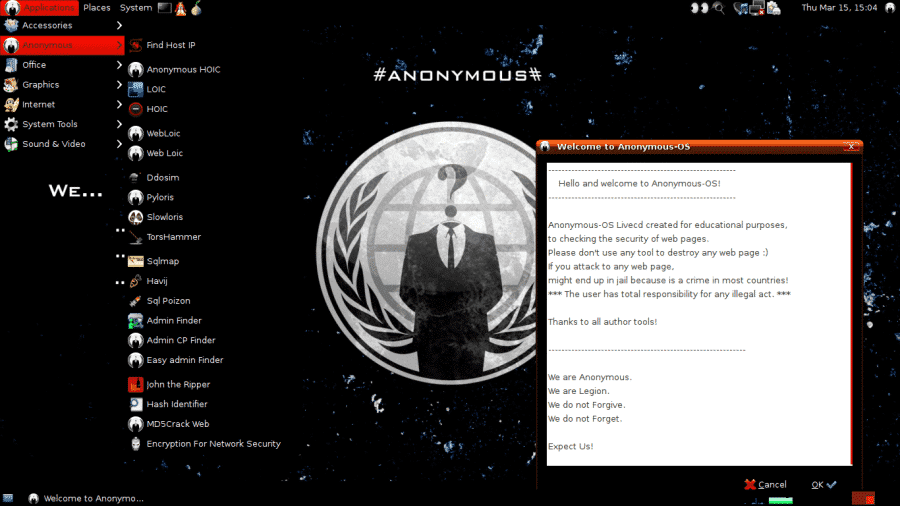
Live hacking OS is a famous free OS of Linux distribution among many people on Pentesting side. According to the Live hacking OS team, we found GNOME default as the desktop environment of this OS.
Not only that, another reason why this OS is special is that it does not require so many resources to run it and it is very important for pentesting, DNS enumeration, reconnaissance, foot-printing, password cracking and network sniffing.
Many tools are included in this.
Fedora Linux
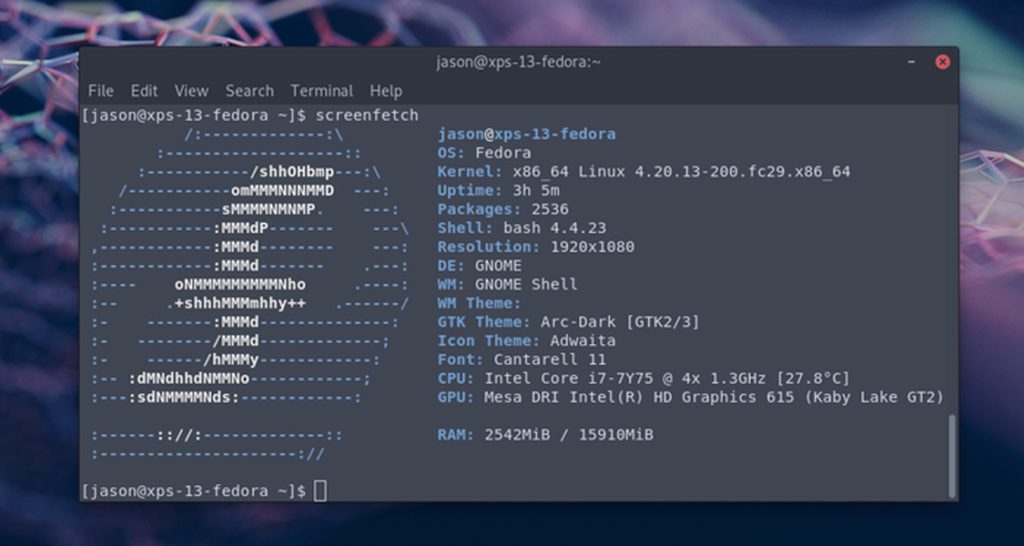
Fedora Linux is also an Open Source OS which is very important for pentesting like the OS we talked about earlier. This is also a Linux distribution just like the OS we talked about earlier. The first release of this OS was on November 6, 2003.
Not only that, Red Hat has helped a lot to develop this OS. According to the team that created Fedora Linux, we can use GNOME as the desktop environment of Fedora OS.
Not only that, as the developers of this OS say, it has become very easy to work with this OS as it comes with inbuilt software required for pentesting like Wireshark, Medusa, Nmap, Etherape, Sqlninja, Yersini.
NodeZero

What is this NodeZero?.
Nudo Zero is also an open-source Linux kernel-based ethical hacking OS. According to the team that created NodeZero, we can use GNOME as the desktop environment of NodeZero OS.
The special thing about this OS is that it has more than 300 tools related to pentesting. Meanwhile, alive6, detect-new-ip6, dnsdict6, dos-new-ip6, fake-advertise6, fake-mipv6, fake_mld6, fake_router6, implementation6, implementation6d, parasite6, recon6, redir6, smurf6, sendpees6, smurf6, toobig6, etc. tools have become famous among many people.
Darcos Linux
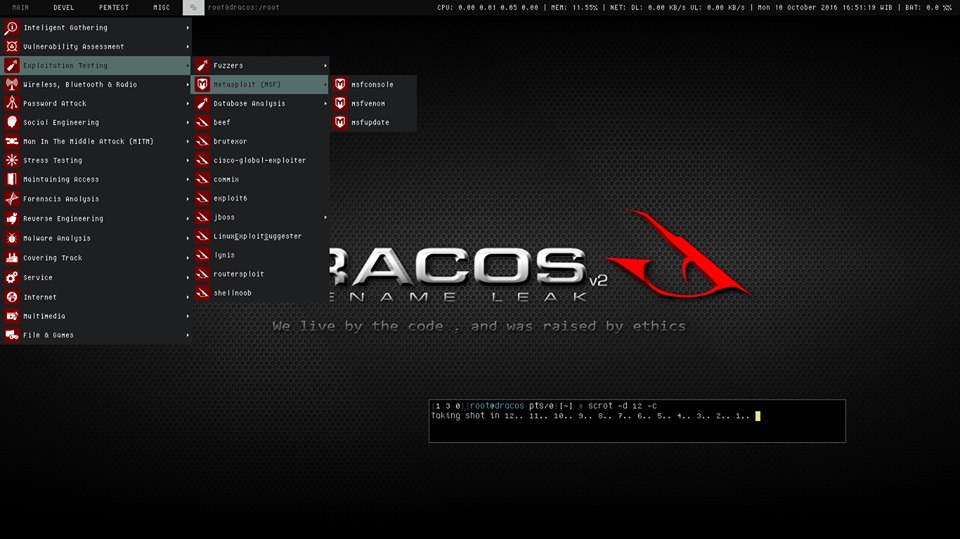
Darcos Linux is a Linux distribution developed by an Indonesian team in 2015. Like the OS we talked about earlier, this also includes many hacking tools. Currently, many people use Darcos OS for things like information gathering, malware analysis, and maintaining access.
To do these things, many tools like ISC DHCP, rfkill, ATK, gdk-pixbuf, Pango, GLib, libjpeg-turbo, libpng, libTIFF, Xorg Libraries, fontconfig, and Cairo have been included in Darcos OS.
Weakerthan Linux
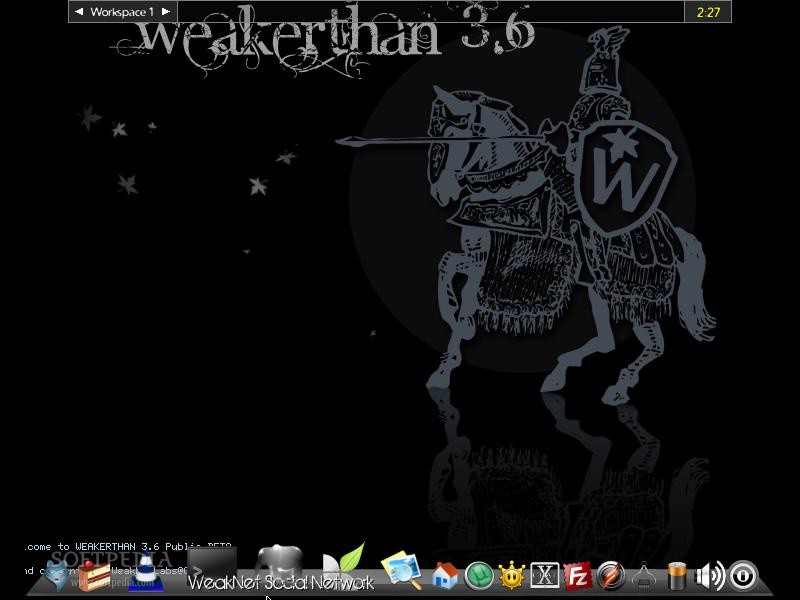
Ok now let’s see who this Weakerthan Linux is.
Weakerthan Linux is also an Open Source OS which is very important for pentesting like the OS we talked about earlier. Also, this is also a Debian-based Linux distribution.
This OS has been developed by the team including Douglas Berdeaux. Not only that, they have mentioned in documents related to this OS that Fluxbox can be used as a desktop environment.
If we look at the performance of Weakerthan OS, we can take care of many wireless hacking tools. Not only that, this OS includes many things like Wi-Fi attacks, SQL Hacking, Cisco Exploitation, Password Cracking, Web Hacking, Bluetooth, VoIP Hacking, Social Engineering, Information Gathering, Fuzzing Android Hacking, Networking and creating Shells. By now, it has become famous among many people.
Arch Linux
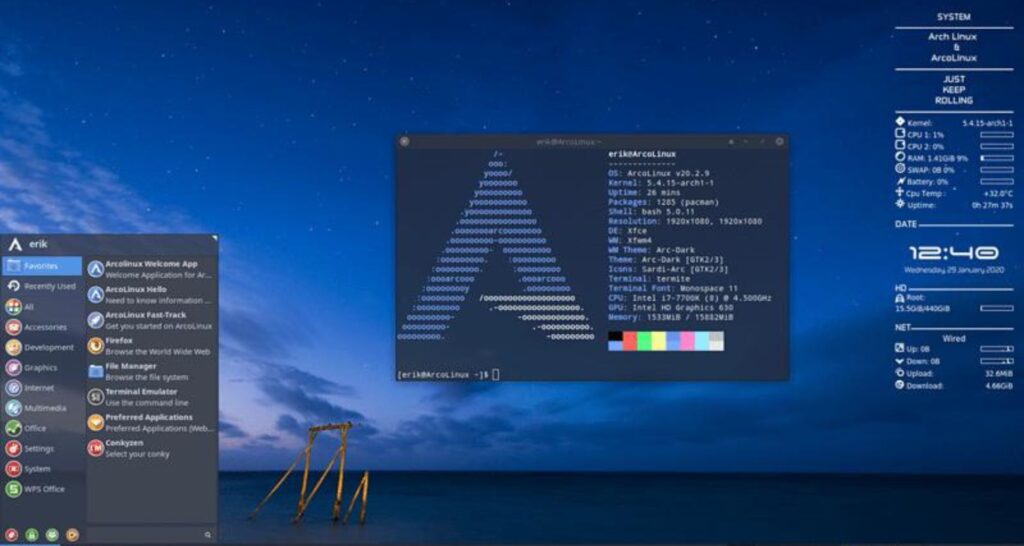
The last hacking OS we will talk about in this article is called Arch Linux. This is also an Arch based Linux distribution that helps in penetration testing like the OS we talked about earlier. And this is an Open Source OS. Developers including Levente Polyak have developed Arch Linux. That was in March 2002.
But if you install this, you must use a device with a processor speed of *84-64. Because, they have mentioned it as a system requirement. And when you take Arch Linux, there are currently about 68,000 source packages. Therefore, users have been able to work easily.
So these are the trending hacking OS (Operating Systems) that many people are currently using. We have a lot to learn from all this. If you are a person who wants to come to the hacking side, you must definitely get the experience of these OS.