In today’s article, let’s talk about who the red team, blue team and purple team are.
The main objective of the security team of any company or organization is to protect the infrastructure of the company / organization. This is just like a team sport. We cannot do this alone. Before the real attacker enters the system, penetration testers detect the vulnerabilities of the system by detecting the attacker’s actions. First of all, we said that this is a team work. That is what we call red team, blue team and purple team.
Red team and blue team are the people who are there to detect the weakness of the system and find out the vulnerabilities. Read team members always work as attackers. The blue team is there to protect the system from the red team. It is correct to say that Purple team is a separate group.
Red Team: Simulating the Enemy
The Red Team operates on a simulated battleground, adopting the tactics of malicious actors to pinpoint vulnerabilities within an organization’s digital infrastructure. This strategic approach enables proactive identification and fortification against potential cyber threats.
Tactical Assessment and Vulnerability Exploitation
Armed with a sophisticated toolkit, the Red Team meticulously assesses an organization’s security posture. Through ethical hacking and simulated attacks, they exploit vulnerabilities, providing invaluable insights to strengthen the overall defense mechanisms.
Real-World Simulation
The Red Team doesn’t merely focus on theoretical vulnerabilities; it engages in real-world simulations, mimicking the intensity of actual cyber attacks. This hands-on experience ensures a comprehensive understanding of potential risks and loopholes.
The Cat-and-Mouse Game: Red Team vs. Blue Team
In the cybersecurity arena, the Red Team’s actions are complemented by the Blue Team’s defensive strategies. This cat-and-mouse game creates a dynamic ecosystem where constant adaptation is the key to success.
Continuous Improvement
As the Red Team exposes vulnerabilities, the Blue Team responds with swift countermeasures. This iterative process of attack and defense fosters a culture of continuous improvement, ensuring that security protocols are always one step ahead.
A Collaborative Approach: Purple Teaming
Recognizing the synergy between offense and defense, organizations increasingly embrace Purple Teaming. This collaborative approach amalgamates the Red and Blue Teams, creating a unified front against cyber threats.
Elevating Cybersecurity Posture
In a digital landscape fraught with risks, the Red Team stands as a beacon of proactive defense. Their efforts not only identify weaknesses but also empower organizations to fortify their cybersecurity posture.
Strengthening Defenses
By embracing the insights gained from Red Team assessments, organizations bolster their defenses. This strategic reinforcement ensures a resilient infrastructure capable of withstanding the ever-evolving tactics of cyber adversaries.
Securing the Future
In the relentless pursuit of cybersecurity excellence, the Red Team plays a pivotal role in securing the digital future. Their expertise and real-world simulations contribute to a collective resilience that safeguards against emerging threats.
Blue Team: Guardians of Digital Frontiers
Championing the cause of defense, the Blue Team stands ready to thwart cyber threats. Their primary objective is to secure and maintain the integrity of an organization’s digital infrastructure against a barrage of potential attacks.
Rapid Response to Red Team Insights
Building upon the insights provided by the Red Team’s simulated attacks, the Blue Team orchestrates rapid response strategies. This includes patching vulnerabilities, refining security protocols, and implementing robust measures to neutralize potential threats.
Proactive Defense Measures
In a cybersecurity landscape characterized by constant evolution, the Blue Team adopts a proactive stance. Regularly monitoring networks, analyzing system logs, and conducting vulnerability assessments are integral components of their defense strategy.
The Symbiotic Dance: Blue Team vs. Red Team
As cyber threats advance, the relationship between the Blue Team and the Red Team takes center stage. This symbiotic dance creates a dynamic environment where each move is a step towards enhancing overall cybersecurity resilience.
Iterative Improvement
The Blue Team’s response to simulated attacks is not a one-time affair; it’s a continuous process of iterative improvement. Learning from each encounter, they fine-tune their defenses, ensuring that the organization remains adept at countering evolving threats.
Collaborative Synergy: Purple Teaming
Recognizing the need for a united front, the Blue Team embraces Purple Teaming. This collaborative approach involves integrating the strengths of both the Red and Blue Teams, fostering a culture of shared knowledge and heightened defense.
Elevating Cybersecurity Resilience
In the face of ever-growing cyber threats, the Blue Team’s efforts are instrumental in elevating cybersecurity resilience to new heights.
Holistic Defense Strategies
Beyond immediate response measures, the Blue Team focuses on holistic defense strategies. This includes developing and implementing incident response plans, conducting regular security awareness training, and fostering a cybersecurity-conscious organizational culture.
Adapting to Emerging Threats
The dynamic nature of cyber threats requires the Blue Team to remain adaptable. By staying ahead of emerging threats through threat intelligence and continuous training, they ensure a proactive defense posture.
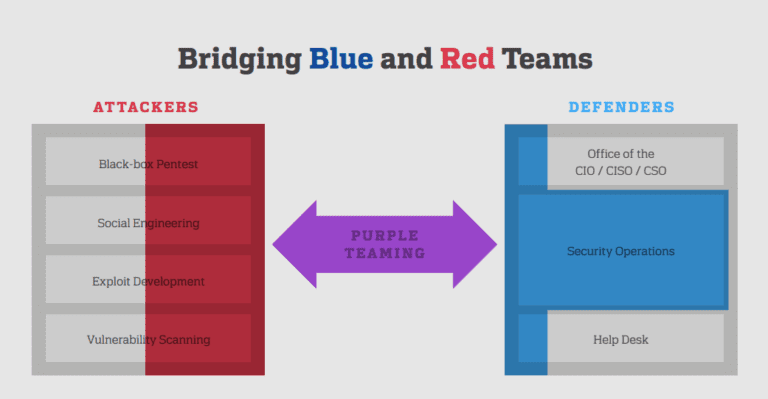
Purple Team: Uniting Offense and Defense
At its core, the Purple Team represents a fusion of offensive and defensive strategies. By combining the expertise of both the Red and Blue Teams, this unified force creates a synergy that is greater than the sum of its parts.
Collaborative Resilience
The Purple Team operates on the principle that collaboration is the cornerstone of cybersecurity resilience. Through joint exercises, knowledge-sharing, and continuous feedback loops, they reinforce the organization’s ability to navigate the complex terrain of evolving cyber threats.
Real-Time Adaptive Strategies
In an era where cyber threats mutate and adapt at an unprecedented pace, the Purple Team’s real-time adaptive strategies shine. By leveraging the insights gained from both simulated attacks and defense mechanisms, they craft nuanced and effective responses to emerging threats.
The Dynamics of Purple Teaming
The relationship between the Red Team, Blue Team, and Purple Team is a dynamic dance, each element contributing to a robust cybersecurity posture.
Offensive Insights Meet Defensive Expertise
The Purple Team acts as a bridge, ensuring that offensive insights from the Red Team are seamlessly integrated with the defensive expertise of the Blue Team. This collaborative approach fortifies the organization against a spectrum of cyber threats.
Continuous Improvement Culture
Embracing a culture of continuous improvement, the Purple Team fosters an environment where learning from every simulated attack and defense maneuver is paramount. This iterative process ensures that the organization is always on the cutting edge of cybersecurity practices.
Elevating Cybersecurity to Unprecedented Heights
In the ever-evolving landscape of cyber threats, the Purple Team stands as a testament to the power of collaboration and strategic thinking.
Enhanced Threat Intelligence
Through the combined efforts of the Red, Blue, and Purple Teams, organizations gain access to enhanced threat intelligence. This comprehensive understanding of the threat landscape enables proactive defense measures.
Empowering Organizations for the Future
By uniting forces and harnessing the strengths of both offense and defense, the Purple Team empowers organizations to face the future with confidence. Their collaborative approach not only mitigates current risks but also positions the organization as a proactive force against emerging threats.
What are the characteristics of red team and blue team?
| Red Team | Blue Team |
|---|---|
| They are called offense security professionals. | They are called defense security professionals. |
| They have the ability to attack the system and brake the system. They use different tools for this. | They have the ability to maintain the system so that attacks do not come. (They do things like firewalls configurations, network configuration.) |
| The red team can be people from the organization itself, or they can be people hired from outside. | They are bound to prevent the attacks from the red team and the actual attacks. |
The process of the Red team and the Blue team is really like a cat and mouse game. Because the mouse always tries to protect his life, the blue team always tries to maintain the security of the company.
If you want to join the red team, you have to think like a hacker, and you have to keep a good practice on how to use security tools. How to plan attacks? You have to think about how to do them. Also, after making an attack, you must have the necessary documentation knowledge to give a full document about it.
If you are going to join the blue team, you have to think about how to protect the system from the red team and real attacks. Before an attack comes, the organization must do the necessary things to protect the company from attacks. (virus guard protection, security controls) and always monitor security controls. According to that, if the current security is not enough, the required security should be provided.
You know that although there are two teams called red team and blue team, the main goal of both teams is the same. That means ensuring the security of the company’s organization. So, because of this, the red team and the blue team do not let the other team know their team’s secrets.
But you know that normally organizations and companies have to give audit documentations about what they do. The purple team is needed for that process.
The Red team documents the log details of the operations they performed. The blue team is documenting how the blue team responded to the attacks from the red team.
We said earlier that the blue team and the red team do not share the secrets of the teams. Therefore, there are many disadvantages for companies and organizations. So the purple team came as a solution to that. Purple team is a combination of red team and blue team.
The purple team talks about the offensive and defensive techniques of the red team and the blue team and prepares a good feedback document. So, as a result of that, the company or the organization will have a good opportunity to protect itself from future attacks.
Now you may have a good idea of red team, blue team and purple team. In the next article, we will talk about something new like this.
The Red Team simulates cyber threats to identify vulnerabilities in an organization’s security infrastructure, contributing to a proactive defense strategy.
The Blue Team rapidly responds to simulated attacks by patching vulnerabilities, refining security protocols, and implementing measures to neutralize potential threats.
The Purple Team unites offensive insights from the Red Team with the defensive expertise of the Blue Team, fostering a collaborative approach to cybersecurity resilience.
Regular Red Team assessments are crucial for staying ahead of emerging threats, and frequency should align with the organization’s risk tolerance and evolving threat landscape.
Yes, Purple Teaming can benefit organizations of all sizes by creating a collaborative and proactive approach to cybersecurity.