Kali Linux is a computer operating system based on Debian, a free and open source operating system. Today, Kali Linux is managed by the IT firm Offensive Security and was developed by Mati Aharoni and Devon Kearns specifically for network analysis, penetration testing, hacking and various cyber security tasks.
Kali.org, the official website of Kali Linux, was not known to many people in the early days, and the website was mostly used by people who were familiar with Kali Linux and worked with Kali Linux. But later this site became more popular with the tele-serial called Mr.Robot.
When doing activities like penetration testing and hacking, those operations have to be executed automatically. Because there are hundreds of operations in such activities and testing takes a lot of time. So, if you go to do these manually, the time taken by the app will increase and you may get bored with the work. That’s why there are many tools that come with Kali Linux to perform operations automatically. These tools save your time and get the right data, perform the operations correctly and give the right results. Kali Linux contains over 350 tools for penetration testing and hacking.
We are going to talk about the best, top 10 tools that can be used for penetration testing and hacking from the tools available in Kali Linux.
Burp Suite
This is used as a Burp Suite proxy which is the most popular and widely used web application security checking tool. That means all the requests go through the browser in this proxy. So we have the ability to change the requests that go through this burp suite as needed. Then it will be possible to identify vulnerabilities in the web such as XSS and SQLi in testing.

Although you can use the community edition of the Burp suite in Kali Linux for free, if you can buy the premium version of the burp suite professional, you can get many valuable features that are not available in the free version.
To use the Burp suite you can follow these steps below.
- First you have to learn how to setup the Burp suite.
- After that, open the terminal and type “burpsuite”.
- Go to the proxy tab there and switch on the interceptor.
- Now you can view any URL and see the request received from it.
Nmap
Nmap is an open network scanner tool used for reconfiguring and scanning networks and it can find things like ports, hosts and services in a network. This sends data packets to the host and checks the output received in response. Also, the Nmap tool has the ability to check and find hosts, identify operating systems and scan open ports. Therefore, this tool can be called the most used tool in that category.

Now let’s see how to use this Nmap tool. For that you have to follow the below steps.
- First we have to give the ping command to get the IP and ping the host. (ping hostname)
- After that open the terminal and give the following command (nmap -sV ipaddress
- Instead of the IP we get now, we need to give the IP we want to scan.
- Then you can get all the details of the respective host.
Wireshark
Wireshark is a network security tool used to monitor and analyze data exchanged over a network. It has the ability to check the data packets circulating in the network. There are several things contained in the data packets that circulate like this. They are the source, the destination IP address, the protocol used and various headers etc. The file type of these data packets, that is, the file type belongs to the extension “.pcap”. So these data packets can be read with the wireshark tool we are talking about.

Now let’s see how to use this Wireshark tool. You have to follow the following steps.
- First, open Wireshark and download a demo pcap.
- Then press “ctrl+o” to open a pcap file with Wireshark.
- Then you can see the list containing the information of the packets and their headers circulated in the network.
Metasploit Framework
Metasploit is an open and free software tool developed by Rapid7. This is the most widely used tool for penetration testing worldwide. This tool has the ability to catch various risky things in a network or operating system and go through them. Metasploit is often used in local networks and has the ability to do port forwarding over the Internet. This is mainly a command line tool and it has a GUI called “Armitage”, which means Graphical User Interface. This makes using Metasploit even easier.
To use Metasploit you can follow below steps.
- Metasploit comes out of the box with Kali Linux.
- Type “msfconsole” in Terminal and enter.
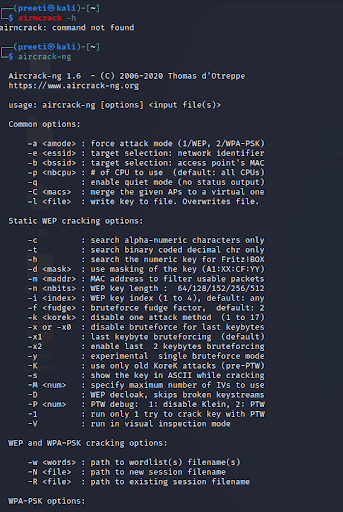
Aircrack-ng
Aircrack is a packet sniffer, WEP, and WPA/WPA all-in-one analyzer tool as well as a hash capturing tool. Accordingly, by using this tool, it is possible to select packages and read their hashes, as well as perform attacks using dictionary attacks. And it supports all modern wireless interfaces.

Now let’s see how to use this Aircrack tool.
- This tool comes with Kali Linux.
- Type “aircrack-ng” in the terminal to open it.
Netcat
This tool called Netcat is used to work with ports. There it performs tasks like port scanning, port listening and redirection. Debugging and network daemons testing are done with this command. This tool is known as swiss army knife among networking tools. This is used to implement TCP, UDP and UNIX-domain sockets as well as open remote connections.
John the Ripper
John the Ripper is an excellent tool used to crack passwords and operations can also be carried out through brute-force attacks such as dictionary attacks and custom wordlist attacks. Also, using this tool, it is possible to find hashes and passwords of locked files as well as zipped and compressed files. Because of this, there are many options to capture hashes and passwords.
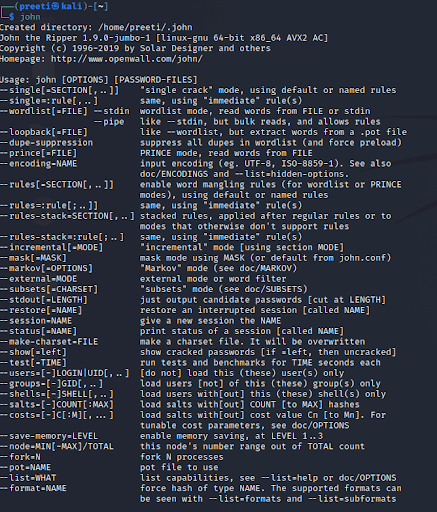
You can follow below steps to use John the Ripper tool.
- Kali Linux comes with the John the Ripper tool.
- It can be obtained by typing “john” in Terminal.
Sqlmap
Sqlmap is one of the best tools that can be used to perform SQL injection. This will automatically perform testing for SQL injection as well as catch dangerous parameters. This is a very useful tool that will automatically run on the database. That being said, we will check the URL provided and automatically check all the risk conditions in the URL. Also, we have the ability to check the requested file and make POST arguments.
You can follow the below steps to use this tool.
- You get this tool with Kali Linux.
- Therefore, it is possible to open this by typing “sqlmap” in the terminal.
Autopsy
Autopsy is a digital forensics tool that can retrieve data from forensics. Simply put, with this tool, we can analyze the files and logs in the system and check how they work with the system. And it can recover data from a pen drive or memory card.

You can follow the below steps to use this tool.
- You get this tool like other tools with Kali Linux.
- You can open it by typing “autopsy” in the terminal.
- Then you can use it by visiting http://localhost:9999/autopsy
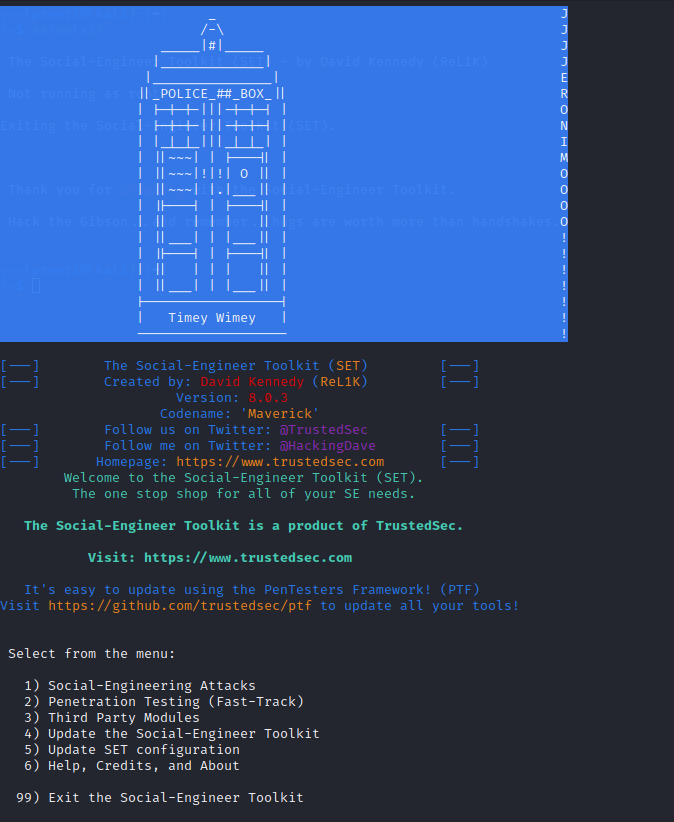
Social Engineering Toolkit
We can call this as a tool with many devices needed to carry out Social Engineering attacks. While this tool has the ability to observe human activities and behavior and collect information, it is a very valuable tool that can even be used for phishing websites. This is an open and free tool and it is also special that it can be used for penetration testing in Social Engineering.

These SET tools have the ability to deliver precise attacks reliably in seconds. Now let’s see how to use this tool. For that you can follow below steps.
- You get this tool with Kali Linux.
- You can open it by typing “setoolkit” in Terminal.
- After that you will have the opportunity to agree to the terms and conditions and use this tool.